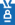Click Injection Explained: How To Combat Mobile Ad Fraud For High-Quality User Acquisition?

Domains that rely on the mobile industry have soared in terms of user-base as well as profit figures. Mobile-based advertisement domain follows a similar story. However, being infected by frauds like click injection, bots, etc., it fails to help advertisers realize the true ROI per its actual potential.
According to a report by eMarketer, mobile internet ad expenses are expected to touch $195.55 billion in 2019, which counts for 70.01% of total digital ad spending. The industry expects a growing trend with mobile ads in the coming years. So passionate marketers like you have the right opportunity to innovate with the trend and deliver the optimum ROI. However, you got to overcome a major challenge in the process – mobile ad fraud.

Type of Ad Fraud
Two categories of mobile ad fraud that have been plaguing the mobile advertising industry in various ways are:
Attribution fraud
Attribution fraud is when the fraudster manipulates the attributions to steal the credit from the actual source of install. Some of the commonly known attribution frauds are:
- Click Injection
- Click Spamming
- Ad Stacking
Install Fraud
When the installation of the app is not executed by genuine users, then it is known as install fraud. Some of the popular types of install fraud are:
- App Install Farm
- SDK Spoofing
- Evasion Technique
In this article, we will discuss click injection fraud, which is one of the earliest fraud type discovered in the app install industry.
What is Click Injection?
As a marketer who is handling user acquisition, click injection is probably the fraud that you experience the most, regardless of if you have figured it out yet or not. In the click injection, a malicious app will impose the click to run your app after installation and to claim attribution for installation at Mobile Measurement Platform (MMP). Hence, the attributes are manipulated and you will be paying the wrong media source instead of the actual (and deserving) source.
How Does Click Injection Work?
Users may unintentionally install the malicious app that performs non-suspicious operations, such as auto-change wallpapers, flashlight, cat-voicing, etc., and it would appear harmless to them. These malicious apps are usually available on unverified Android sources for free. They can even make their way to mobile devices without letting the users know. Such apps have permission to inject a click to run another application and to listen to the ‘install broadcast’.
- ‘Install broadcasts’ are the signals sent by apps installed on Android devices to update the status like installation or uninstallation.
The malicious app installed in the phone keeps performing its unsuspicious action until it listens to an Install Broadcast. On finding an Install Broadcast of your app, it sends a click to the MMP to claim itself as the source of app install and also injects the click to run the application. In the advertising process that involves Cost Per Installation model, advertisers pay mostly to the last source that got the successful installation. In this model, the malicious app is able to stake the claim on the credit of getting your app installed.
Who Is Affected By Click Injection Fraud?
Almost every stakeholder in the advertising is affected by Click Injection fraud, even if the respective consequences may vary. It marginally affects the user experience of the customers, while if you are a network, publisher, and advertiser, the impacted is big – in terms of money as well as reputation.
Networks and Publishers:
Click injection fraud will take away the credit from the worthy network and publisher, so you will not be able to make money even if you got an install from your genuine efforts.
Considering that the publisher or network inflicts the fraud, they will be at some loss as well. This is because they will be paying some amount to the fraudster, which otherwise would have been entirely theirs.
Advertiser:
It might appear that you eventually got the intended result (getting app installed) out of the campaign as an advertiser even if it is influenced by the click injection fraud. However, it impacts them in multiple ways. Firstly, you might end up paying to the network or publisher even if you earned the installation with the organic efforts. Moreover, such ad frauds manipulate the campaign performance report.
It can negatively impact the decision making as you may keep spending more on fraud-based sources while the real performers will be downsized. Needless to mention, that’s not an ideal situation to be in.
| Similar reading suggestion: Click Fraud Prevention – Identify & Reduce Bot Traffic in Your Paid Ads |
How to Minimize Effects of Click Injection In Your Ad Campaigns
Data Analysis:
The data patterns for the normal app installs and Click-injected installs are different. A closer look at the data to identify these pattern discrepancies can help you detect the fraud.
Average Click To Install Time (CTIT) is a factor to determine the click injection fraud in your ad campaigns. For the fraud-proof cases, most installations should be within the range of average CTIT. Average CTIT can be calculated relying on the APK file size, network strength, etc.
For the fraud-affected cases, there will be a sudden peak in the number of installations during the time range less than average CTIT. Some of the apps try to manipulate this pattern by defining a certain time range after which it opens the app.
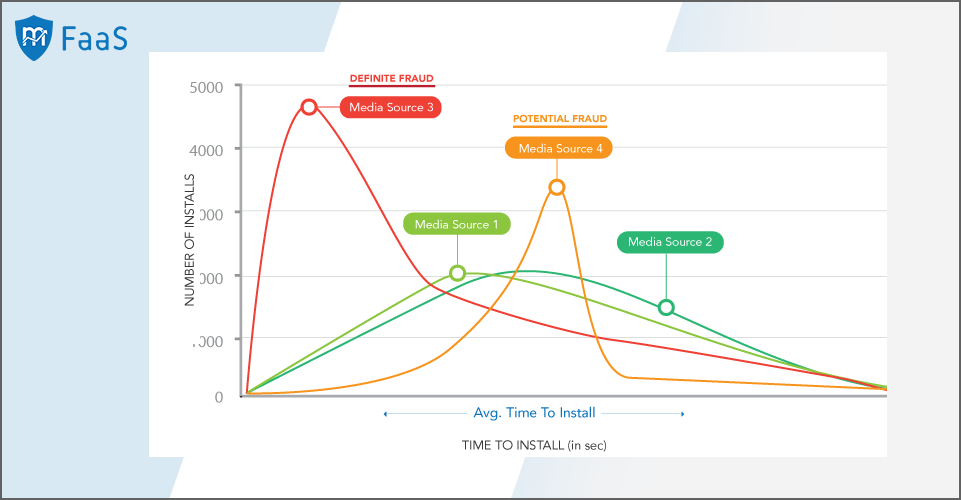
Interpreting the graph:
- Media Source 1 and Media Source 2 follow a consistent installation Time to Install pattern and therefore, are likely to be delivering fraud-free app installations.
- Media Source 3 indicates a low time to install, which proves the use of bot or click injection. So, it is a definite fraud.
- Media Source 4 has a sudden spike at a particular time duration, which hints at the possibility of abnormal traffic behavior. The script injects the click at a certain point of time to make it appear normal. So, Media Source 4 could be a potential case of fraud.
Choosing Reliable Partners for Marketing
If you are buying the media sources that promise to deliver the app installs at an unbelievably low price, there is a strong chance you will end up getting fraudulent installs. Even though the rates may vary for different industries, delivering the installs with ethical methods comes at a cost. The smart option will be to do adequate market research before choosing media sources.
Fraud Detection Solution
There are fraud detection solutions that can detect and block the frauds in real-time. Along with the pre-defined algorithms to identify the data anomalies, there are tools with machine-learning that can keep on upgrading their metrics to mitigate the frauds. Such solutions can help you keep an eye on the live campaigns and save your expenses on them that are draining down to unwanted or fraudulent media sources.
mFaaS, one of the popular mobile ad fraud detection solutions, not only keeps track of your live campaigns but also looks into historical fraudulent media sources to assign a fraud score to each campaign based on 15+ reason codes. With such stringent multiple checks and filters of mFaaS, marketers find it easier to identify and block possible ad frauds in their campaigns.